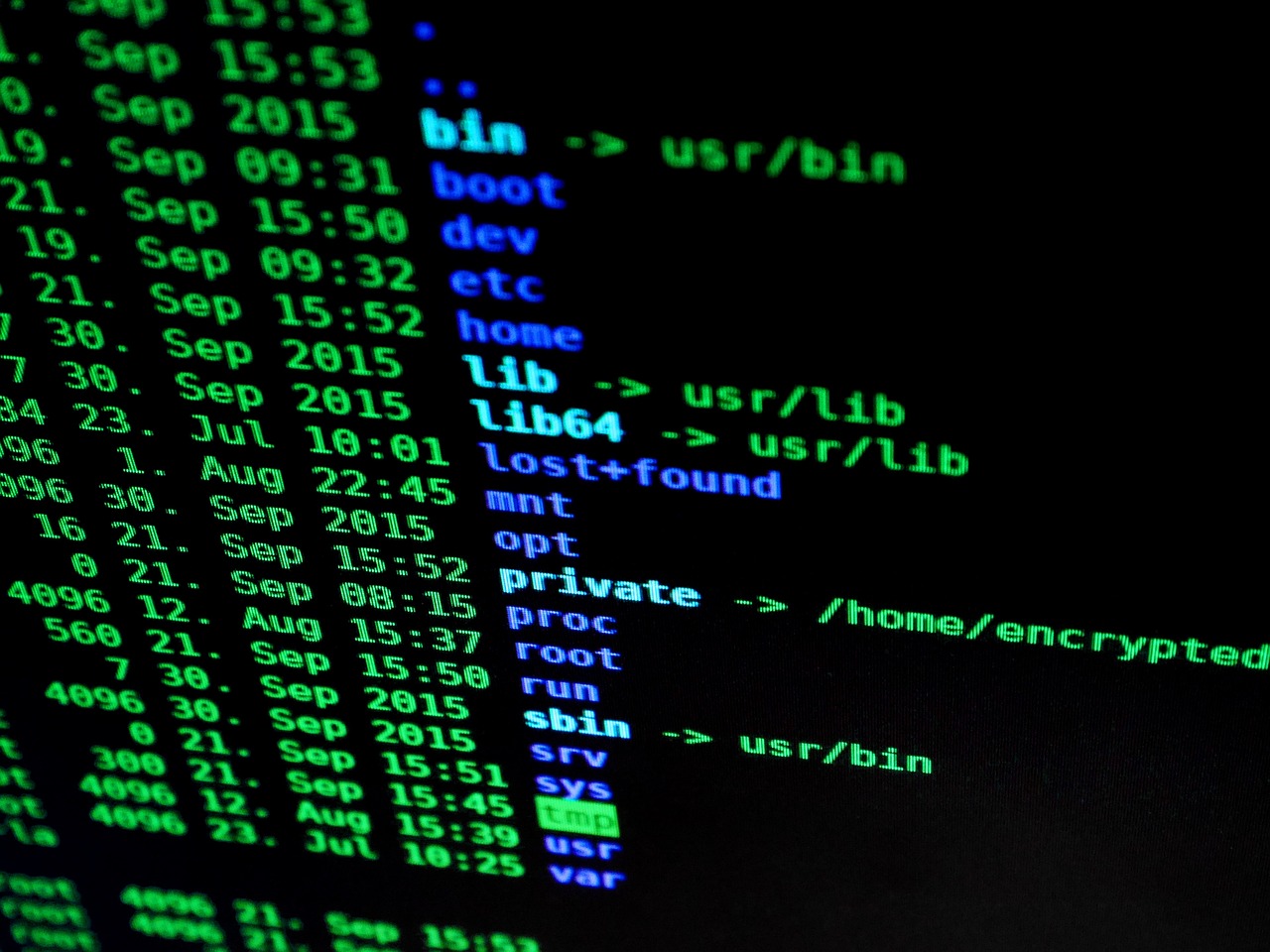
Best Software Reverse Engineering Tools
Table of Contents
- Introduction
- What is Reverse Engineering?
- Top Reverse Engineering Tools
- Choosing the Right Tool
- Ethical Considerations
- Conclusion
Introduction
As a cybersecurity professional and software developer with years of experience in reverse engineering, I’ve learned that having the right tools can make all the difference between a successful analysis and a frustrating dead end. Reverse engineering is an art form that requires precision, patience, and most importantly, powerful software that can unravel complex binary mysteries.
In this comprehensive guide, I’ll walk you through the most potent reverse engineering tools that have been my trusted companions throughout my career. Whether you’re a pentester, security researcher, malware analyst, or curious developer, these tools will become your digital Swiss Army knife for software exploration.
What is Reverse Engineering?
Reverse engineering is the process of analyzing a system, software, or hardware to understand its inner workings, design, and functionality. It’s like being a digital detective, meticulously deconstructing code to reveal its secrets. In my experience, reverse engineering serves multiple critical purposes:
- Security vulnerability research
- Malware analysis
- Software interoperability development
- Legacy system understanding
- Performance optimization
- Competitive technology analysis
Top Reverse Engineering Tools
1. IDA Pro
Website: Hex-Rays IDA Pro
IDA Pro is the gold standard in reverse engineering tools. I’ve used it extensively in my professional work, and it’s like the Ferrari of disassemblers. Key features include:
- Advanced disassembler and debugger
- Support for multiple processor architectures
- Powerful scripting capabilities
- Comprehensive analysis and visualization
- Hexadecimal and decompilation view
- Extensive plugin ecosystem
Pros:
- Industry-standard professional tool
- Extremely powerful decompilation
- Supports wide range of platforms
Cons:
- Expensive
- Steep learning curve
- Requires significant expertise
2. Ghidra
Website: NSA Ghidra
Developed by the National Security Agency, Ghidra is a game-changer in the reverse engineering world. When it was released, it democratized high-end reverse engineering tools by being completely free and open-source.
Key Features:
- Powerful decompiler
- Cross-platform support
- Built-in scripting with Python and Java
- Collaborative reverse engineering
- Advanced binary diffing
- Extensible through plugins
Pros:
- Completely free
- Government-grade capabilities
- Active community support
Cons:
- Less polished interface compared to commercial tools
- Slightly slower performance
- Steeper initial learning curve
3. Radare2
Website: Radare2
As an open-source reverse engineering framework, Radare2 is a Swiss Army knife for security researchers. I’ve found it particularly useful for low-level system analysis.
Standout Features:
- Command-line based reverse engineering tool
- Multi-architecture support
- Supports numerous binary formats
- Powerful scripting capabilities
- Lightweight and portable
Pros:
- Completely free and open-source
- Extremely flexible
- Works on multiple platforms
Cons:
- Text-based interface can be intimidating
- Requires significant terminal knowledge
- Less user-friendly for beginners
4. Binary Ninja
Website: Vector 35 Binary Ninja
Binary Ninja offers a modern approach to reverse engineering with an emphasis on usability and powerful analysis capabilities.
Key Capabilities:
- Interactive GUI
- Advanced program analysis
- Machine learning-assisted code recognition
- Python scripting
- Cloud-based collaboration
Pros:
- Clean, modern interface
- Excellent for medium-complexity reverse engineering
- Strong Python integration
Cons:
- Moderate pricing
- Less comprehensive than IDA Pro
- Smaller plugin ecosystem
5. OllyDbg
Website: OllyDbg
A classic Windows debugger that has been a staple in the reverse engineering community for years. While it hasn’t been actively developed recently, it remains popular among Windows-focused researchers.
Features:
- Windows-specific x86 debugger
- Intuitive user interface
- Excellent for understanding Windows executables
- Plugin support
Pros:
- Free
- Easy to learn
- Lightweight
Cons:
- Windows-only
- No longer actively maintained
- Limited to x86 architecture
6. x64dbg
Website: x64dbg
The spiritual successor to OllyDbg, x64dbg is an open-source x64/x32 debugger for Windows.
Key Features:
- Modern replacement for OllyDbg
- Support for 64-bit and 32-bit debugging
- Active development
- Plugin architecture
- Excellent for malware analysis
Pros:
- Free and open-source
- Modern interface
- Active community
Cons:
- Windows-specific
- Less comprehensive than commercial tools
7. Hopper
Website: Hopper
Specifically designed for macOS and Linux users, Hopper provides powerful reverse engineering capabilities for these platforms.
Capabilities:
- Disassembler and decompiler
- macOS and Linux focused
- Support for multiple architectures
- Pseudocode generation
- Symbol renaming and commenting
Pros:
- Native macOS/Linux support
- User-friendly interface
- Affordable compared to IDA Pro
Cons:
- Platform-limited
- Less powerful than top-tier tools
Choosing the Right Tool
Selecting the perfect reverse engineering tool depends on several factors:
- Your Primary Operating System
- Specific Use Case
- Budget
- Complexity of Targets
- Personal Skill Level
Ethical Considerations
As a professional, I cannot stress enough the importance of using these tools ethically and legally. Reverse engineering should only be conducted:
- With explicit permission
- For legitimate research purposes
- Within legal and contractual boundaries
- Respecting intellectual property rights
Conclusion
The world of reverse engineering is fascinating, complex, and incredibly powerful. These tools represent the pinnacle of software analysis technology. Each has its strengths, and the best approach is often to become proficient in multiple tools.
Whether you’re a security researcher, developer, or curious technologist, mastering reverse engineering tools opens up a world of deep technological understanding.
Pro Tip: The most powerful tool is always the human mind behind it. Technical skills, curiosity, and ethical practice are your most important assets.
Disclaimer: Always ensure you have proper authorization before reverse engineering any software. Unauthorized reverse engineering can be illegal and unethical.












Comments